IGEL Blog

Preventative Security for your Endpoints – Prevention Is Better Than Cure
IGEL’s Preventative Security Model™ provides a secure endpoint OS for your use case.
It’s clear from the headlines that today’s approach to endpoint security isn’t working: take your OS, install antivirus, the latest XDR and DLP, make a lot of settings, harden that with custom scripts, install your applications, keep updating those applications and the OS and the AV and DLP….. and hope that all these steps keep the wolf from the door and the ransomware out of your systems. Does your business financial data, personal health information or any other data feel secure?
With many of today’s workloads moving from the endpoint to SaaS, DaaS, VDI or being accessed through secure browsers, and many organizations looking at how to apply Zero Trust, isn’t it time to re-evaluate the endpoint?
What if you could put an endpoint OS into your workforce’s hands that was designed for the cloud-first world that doesn’t need high levels of care and feeding to remain healthy? Something that is more robust by its nature, that had built-in preventative components or measures, as in “Prevention is better than cure.”?
IGEL OS applies a number of core principles that make it a secure choice as an endpoint OS – the Preventative Security Model™.
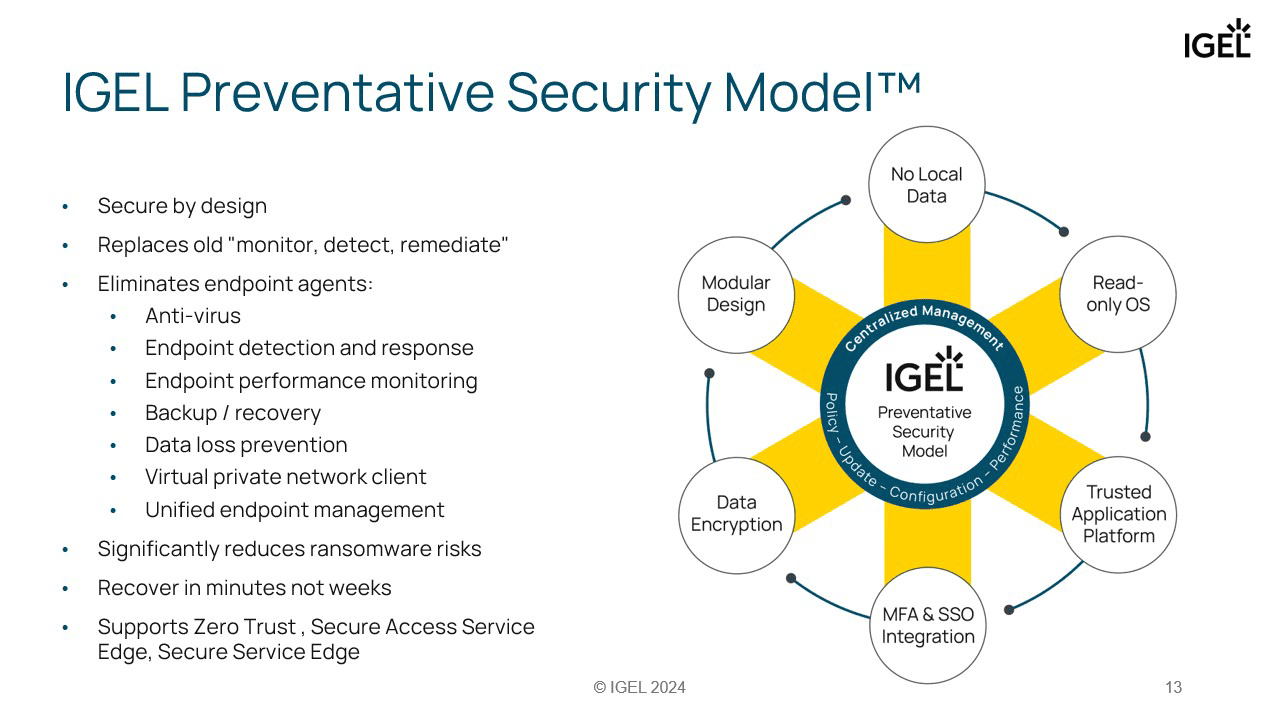
A Safe Place for Your Data
The best place for your business data is definitely not on the endpoint device that could be lost, stolen, left on a plane, Put your applications and data on servers in a data center – whether you call this approach server-based computing, VDI, cloud, DaaS or SaaS. Windows and its applications run great there, SaaS applications have proven to be more secure than the endpoint – patched by professionals, constantly updated, protected by network security, physical security, fire protection, uninterruptible power supplies, backup, failover…
With this approach, your endpoint can run a minimal system that excels in securely enabling access to your hosted workloads. The endpoint now holds nothing of interest for an attacker – ticking the device box for your Zero Trust review.
Encrypted
The configuration information which is the only item of potential value is stored by IGEL OS on a separate disk partition encrypted with industry-standard AES256 in XTS-plain64 mode with 512 bits of key material. If your hardware supports TPM 2.0, IGEL OS will use it to protect the encryption keys.
Read-Only Is Robust
The rest of IGEL OS, its Linux operating system and the programs, are mounted read-only. This means that a user – or malware – can’t change them by mistake or by ill intent. And it also means that malware can’t find a foothold there and persist. Its solid Linux foundation kept NHS hospitals using IGEL OS functioning when many others were brought down by the WannaCry malware wave that affected Windows in 2017.
Additionally, all the disk partitions on IGEL OS are cryptographically hashed and signed. This guarantees they come from IGEL and have not been tampered with. The signatures are checked on every boot, during runtime, and before you install a system update or an IGEL OS app. Also, IGEL uses UEFI Secure Boot with a signed bootloader and Linux Kernel to make sure the booted system is trustworthy.
Endpoint Control
Besides this core OS robustness, IGEL’s Universal Management Suite (UMS) lets you lock down every IGEL’s endpoint to control everything from a system’s network configuration to when the screensaver and screenlock kick in. With the IGEL App Portal, you install only what your staff need to do their work, and nothing more. IGEL native apps are available from Citrix, VMware, Imprivata, Cisco, Okta and more. IGEL OS logs can be forwarded to your SIEM of choice integrating with your monitoring and alerting frameworks for familiar and coherent visibility.
Restore and Update Fast
It is also easy to replace an IGEL OS endpoint that has failed: IGEL ships from the factory on HP, Lenovo and LG devices, or you can IGEL an existing device that you may have to hand within a matter of minutes. A complete factory reset on the existing hardware will pull down its latest configuration and apps from UMS and is ready to be used.
Due to the much smaller IGEL OS footprint, a full system update finishes within a few minutes and can be scheduled outside office hours using UMS. IGEL’s failsafe update keeps the previous system as a fallback should the update fail, maybe because of a power cut. This means that an IGEL OS device will always be able to boot, get on the network and keep employees productive.
Tested and Trusted
To make and keep IGEL OS secure IGEL has a dedicated Security Team and employs a Secure Software Development Lifecycle (SSDLC) that covers all steps from the idea and design of a new feature up to its release in a new product version. It contains in-house tasks as diverse as threat modeling, design review, code review, static and dynamic application security testing and documentation. Additionally, we have all our software undergo independent penetration testing by external providers every year.
Save Time, Money and Nerves
This is, in very short terms, the Preventative Security Model™ of IGEL OS. It is supported by a company with more than 20 years of experience in end user computing and Linux – a company with the experience and knowledge to support you. IGEL will help you save time, money, and nerves, despite the ever-increasing crescendo of security issues clamoring for your attention.


